Fileless Malware
Within the Cyber (crime) area, there are various forms of Malware (malicious software), like Remote Access Tools (RAT), Trojan Horses and Ransomware.
Traditional malware contaminations are usually malware downloaded from the internet and accordingly installed on your computer. When the malware is started up, the malware can serve its purpose. The essential building-blocks for the execution of the malware are built-in the piece of software itself. Traditional malware is therefore often detected by analysing executive programme files, so-called executable binaries. Cybercriminals are, however, never quiet, but they keep innovating themselves. The consequence of this is that lately also other forms of malware have been detected.
Recent in the media
On Wednesday 4 May 2022 Kaspersky, a software company specialised in computer security and antivirus software, issued an inquiry report that paid attention to a new discovery within the malware world, namely hiding malware in a specific part of Microsoft Windows, without additional (practicable) mala fide programmes. This malware was hidden inside the Windows Event Logs. It was the first time that a piece of malware was discovered within that component of Windows.
This article is not so much about the specific situation as described by Kaspersky, but about the phenomenon of Fileless malware in general.
Continuous development Malware
Fileless malware does not have separate practicable programmes. The entire malware remains in the working memory of the computer, also called the RAM (Random Access Memory). Apart from that, basically all references regarding the presence of malware are removed. These references are called footprints. Since these footprints are not, or hardly, present anymore, removing malware is very difficult.
In short, one could say that in case of Fileless malware, it uses the ‘own’ proceedings of the computer, to attack the computer. Programmes that are abused are, amongst others, Windows Management (WMI)2, PowerShell3 and for example Microsoft Office macros4.
In order to explain how Fileless malware works, we use the analysis of Varliogly, S., Elsayed, N., & Murat Ozer, M. (2020). The Dangerous Combo: Fileless Malware and Cryptojacking and we zoom in further on the specific phases. The main features of the phases described by Varliogly et al. can also be found at traditional malware.
Delivery
Within the delivery phase two categories are explained, the exploitations of network related vulnerabilities and the exploitations of a file.
Regarding the exploitation of vulnerabilities via the network, the cybercriminal gets access to the computer via a (un) known vulnerability. Accordingly, the cybercriminal can execute the so-called ‘payload5’ on the machine.
Regarding exploitation by means of a file, the cybercriminal makes adaptations to a file in advance, in order to avoid security and to create initial access. Examples of files that are used to carry this payload are email enclosures, that execute scripts which are loaded in the working memory directly. Another example is hiding a task within Microsoft Office macros.
This task can, for example, collect a file or script from an external location that offers initial access to the cybercriminal. The malware then does not need the infected file anymore to run, and is therefore ‘fileless’.
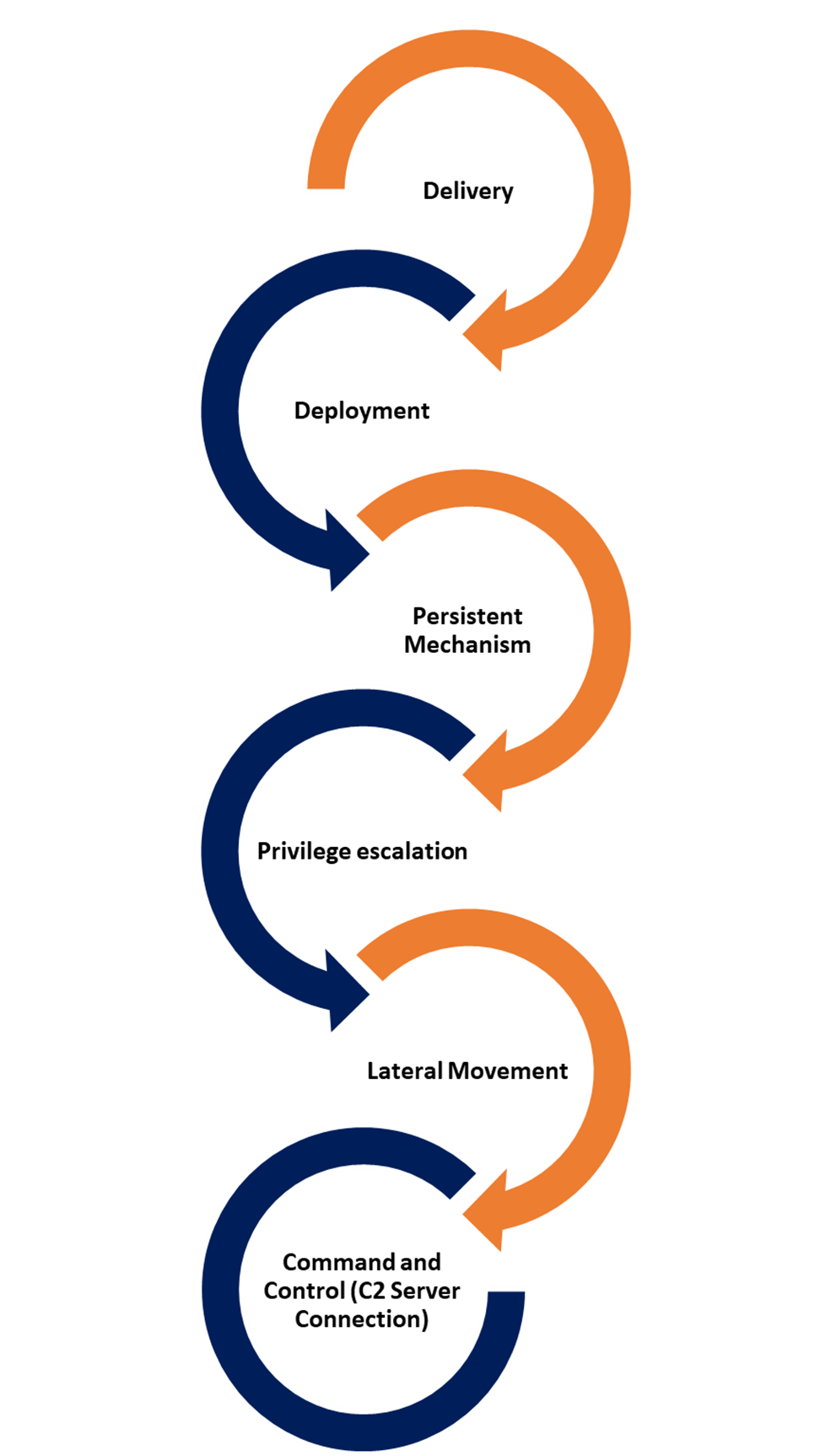

Figure 1: example of a malign macro to create a task out of Word file that was an enclosure of an email. Imagine from Varliogly, S., Elsayed, N., & Murat Ozer, M. (2020). The Dangerous Combo: Fileless Malware and Cryptojacking Page 3, figure 2
Also, the so-called zero-days were said to be used to enter. An example of a zero-day that the media paid a lot of attention to is, is that of Log4j. Such an exploit is then used to gain initial access to the system, after which the Windows own programmes are used to initialize the malware. After all, Fileless malware is all about exploiting Microsoft’s own programmes.
Deployment
In the deployment phase the necessary files, programmes and tasks are approached by the script. Within this phase we often see the use of PowerShell scripting. These scripts are often hidden in a base-64 encoding6. Because of the powerful functions within the Windows PowerShell, the code injections are applied to the legitimate proceedings or auto-start options within the Windows Register7 are approached or altered.
Well-known system administration programmes that are often exploited within Fileless malware attacks are PSEXEC, MSHTA, BITSAdmin, CertUitl, and Msiexec. The further description and application of aforementioned system administration programmes will not be discussed any further in this article.
Persistent Mechanism
After the malware has been executed, the next challenge for the cybercriminal is to maintain lasting access. This is what this phase is about: creating a lasting access to the system. If it is not possible to create this lasting access to the system, a ‘simple’ restart of the system will deny a cybercriminal access to the system.
This lasting access is accomplished in various ways. A combination of PowerShell, WMI, Windows Task planner and the Windows Register are often used to save rules and assignments, which make it possible to keep lasting access; also after restarting the system.
Privilege Escalation
Since the cybercriminal can make use of the higher rights within the Windows system and the accompanying programmes, a lot of actions can be performed within the network. The cybercriminal thus avoids the built-in security mechanism named User Account Control (UAC). In order to obtain the highest rights within a Windows computer system, normally a user should be identified who has these higher rights. Often these accounts are referred to as admin-accounts which are mainly used by system administrators. By the manner in which the Microsoft Windows operating system is built-up, the cybercriminal obtains these rights, because own programmes of the operating system are used. These ‘standard’ programmes have the higher rights within the operating system. Because of the architecture of Windows it is therefore possible to obtain the highest rights from every random user with basic rights.
Lateral Movement
The cybercriminal will always try to end up with the most important computer or server within the network. With regard to this, the cybercriminal will map out the network and will move through the network, step by step, in order to eventually get access to the most important server. This most important server is often called the Domain Controller8. To map out the network, often legitimate Windows programmes are used, such as Adfind.exe9. By performing actions on the server, computer or database that seem legitimate, the cybercriminal can try to become part of the regular traffic (network) to prevent further detection.
Command and Control (C2 Server Connection)
When all previous phases have been followed, the cybercriminal often has been able to create a lasting connection to the network. The cybercriminal can thus approach, advise or control the entire network or part of the network.
The infected machine that malware runs in, is sometimes called a zombie. The term zombie is used for computers in which malware is present and that can be controlled, without the owner or administrator having knowledge of this.
After access has been gained in this way, it may take hours, days, weeks or even months before extra actions are performed within the network. The cybercriminal who stays in the network before his or her presence is detected, is also called the ‘dwell time’. According to results of an inquiry of the (cyber) threat intelligence company Mandiant, in 2021 the cybercriminal stays on average 21 days in the network before he or she is detected. It then often becomes clear what the ‘alternative’ motive of the cybercriminal is for entering the network. This could for example be taken the computers in the network hostage (Ransomware), or stealing data (data leaks) or using the computing power of the machines in the network to mine cryptocurrency. Apart from exploiting the network ‘himself/herself’, it can also be that access is sold to other cybercriminals. The cybercriminal can also be part of a larger criminal organisation, where everyone is responsible for a certain part in the chain.
Conclusion
As you can read, Fileless malware has other characteristic features than traditional malware. The malware works without needing other programmes or services than the part of Microsoft Windows. Scripts with higher rights are also executed without additional mala fide (practicable) programmes, and the cybercriminal thus gains even more control over the system.
Apart from that, traditional detection is not sufficient and removing this form of malware is sometimes very complicated and complex. Nevertheless, on various locations traces can be found back from this malware. This could be task planner, the register, Windows Event logs, or in case of sent data traffic, by the infected machine (zombie). If you suspect malware contamination and you want to inquire this further, it is wise to not restart the infected machine, so the working memory (RAM) will be saved.
Contact
A disruption of business continuity is always undesirable, especially when this is caused by a cyber-attack. Have you been attacked? DataExpert helps! Call 0800-1660.
Do you want to read more about how cybercrime works? Please follow one of our cybercrime training courses. During our cybercrime training courses our trainers discuss how cybercrime works, which traces a cybercriminal can leave and how these traces can be used in an investigation. Do you also wish to know more about analysing (received or sent) data traffic? During the IP-interception training course you learn the basic knowledge reading the IP-infrastructure and you learn to analyse data packages with programmes such as Wireshark.
For more information please go to our website or contact us.
List of definitions:
- Windows Event logs1 keeps a logbook of application and system messages. The Windows Event Logs are a valuable source of information about error messages and system messages.
- Windows Management Instrumentation (WMI)2 is a built-in function since Windows NT. This function provides information in a standardized way to programmes and management scripts. This can be information from the event logbook, the amount of RAM memory, updates and which software is installed on the computer.
- Windows PowerShell3 is a script language that, by means of interactive Command line can configure systems and can computerise tasks. With respect to appearance, it resembles the ‘MS-DOS’ environment, but with far more options and possibilities.
- Microsoft Office macros4 are computerised scripts that can computerise tasks for the user that are often used. It is a series of assignments and instructions that groups as one assignment, in order to automatically perform one particular task.
- Payloads5 refers to the manner in which information is transported over the network (or in a file). Internet traffic is send over the internet via data packages. This can be compared to sending a package. The package has dispatch information (dispatch label). The contents of the package often only become clear after the received opens the package. The payload can be compared to the actual contents of the package.
- Encoding6 means converting details to another format, for example from readable text to a specific input that a certain programme can deal with. Sometimes encoding is used to make it more difficult to see what a certain process does. The opposite of encoding is decoding. With decoding one can, for example, convert specific input back to readable text.
- Windows Register7 is a kind of database within the operating system Microsoft Windows in which settings of the users, programmes, machines and the system itself, are saved.
- Domain Controller8 is a Windows Server organised to monitor rights. Part of this server is the active directory. The active directory is a database. In this database it is registered who has which rights within the network, and everything that is in the network.
- exe9 is a command-line programme to question the active directory.
References:
Cryptojacking. International Conference on Cyber Warfare and Security (ICCWS). https://doi.org/10.1109/ICCWS48432.2020.9292376
Legezo, D. (2022, 6 May). A new secret stash for “fileless” malware. Securelist. Consulted on 24 May 2022, from https://securelist.com/a-new-secret-stash-for-fileless-malware/106393/
Mandiant. (2022, 19 April). M-Trends 2022 (Version 13th) [Insights into Today’s Top Cyber Security Trends and Attacks].